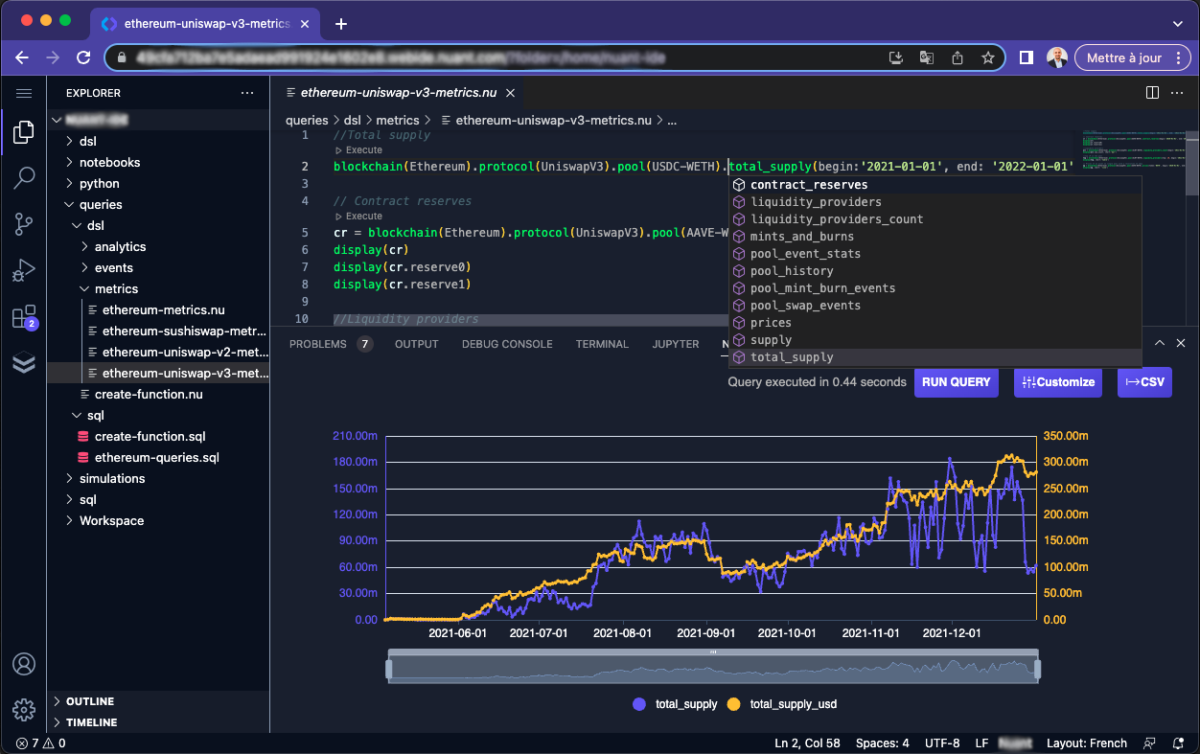
In the blockchain and cryptocurrency industry, leveraging custom metrics and analytics is crucial for the development of risk analysis applications. Traditionally, SQL serves as the primary language for querying precomputed tables, derived from aggregations on raw data extracted from the blockchain. However, this approach can become cumbersome and error-prone, particularly as database schemas grow [...]
Process Modeling & Simulation
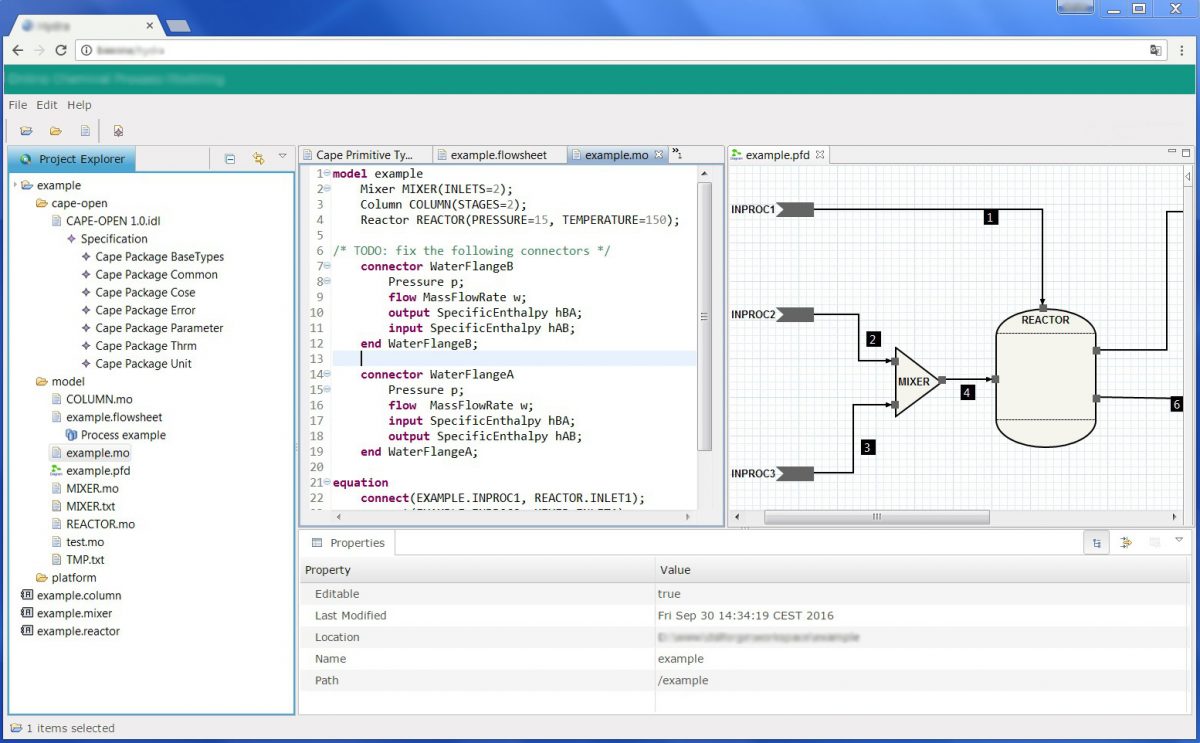
admin 2023-12-07T13:39:47+00:00In the Oil & Gas industry, the use of simulation plays a vital part in developing integrated chemical processes. By helping save time and money before the actual process implementation, this practice can assist with troubleshooting, design, control, and more. Process modeling and simulation typically involves using dedicated software to define a process as interconnected components, [...]
Online Education for K-12
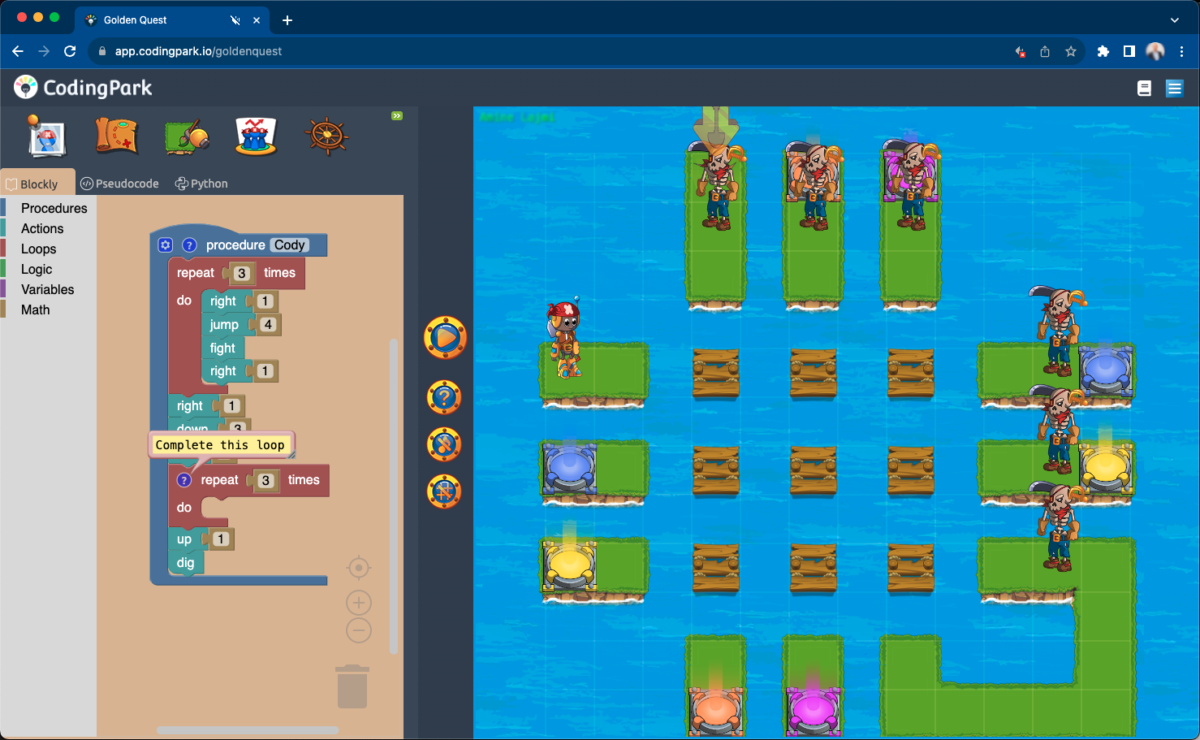
admin 2023-12-07T13:34:08+00:00Software is becoming a critical layer of all our lives; it is the language of the world. In the future, not knowing the language of computers will be as challenging as being illiterate or innumerate today. Computational thinking in particular is how software engineers solve problems, it combines mathematics, logics and algorithms, and teaches [...]