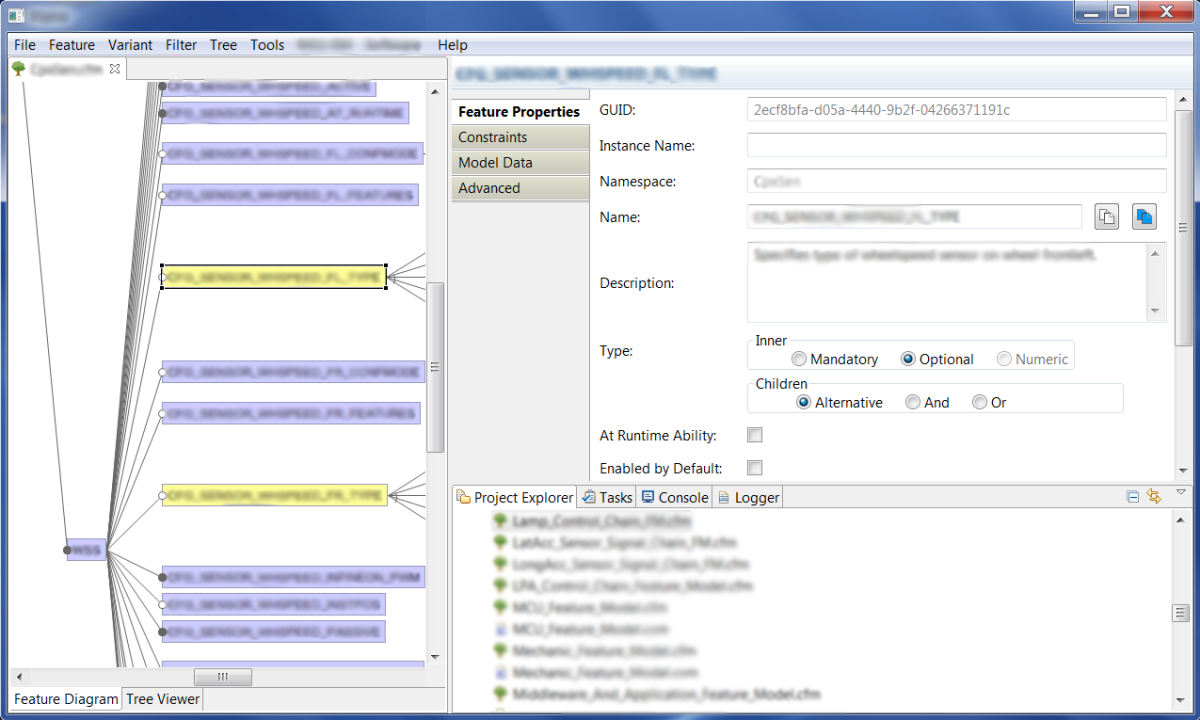
One of the major technical innovations in Software Product Lines is the use of features to distinguish members of product lines. Feature models define the characteristics and the usability constraints in families of products. Current methods organize these characteristics in a tree, or a feature diagram, which is used to declaratively specify the members [...]
Model Synchronization
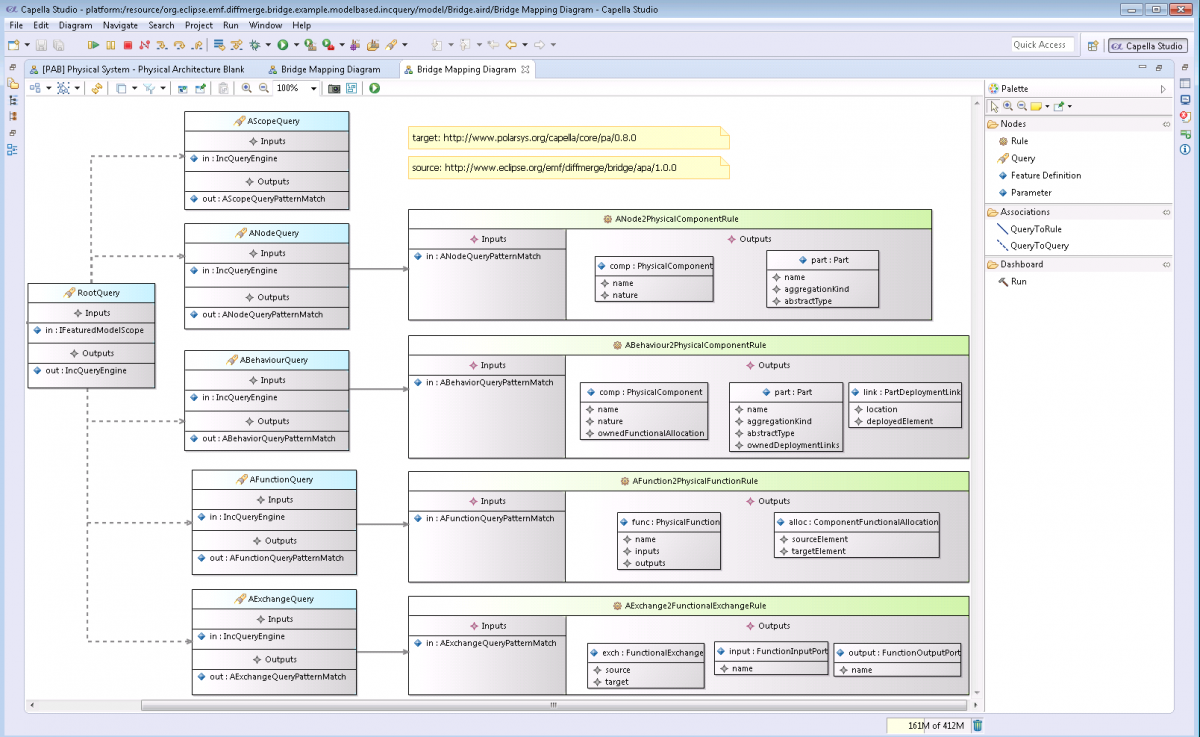
admin 2023-12-07T13:39:38+00:00In systems and software engineering, focus is attached to architectural design activities, so as to reduce efforts and risks before system development. Engineering processes and techniques have evolved to meet these new requirements. Indeed, working at the system architecture levels requires a close collaboration between domain experts, with different languages and practices, and therefore, there is a [...]
Online Education for K-12
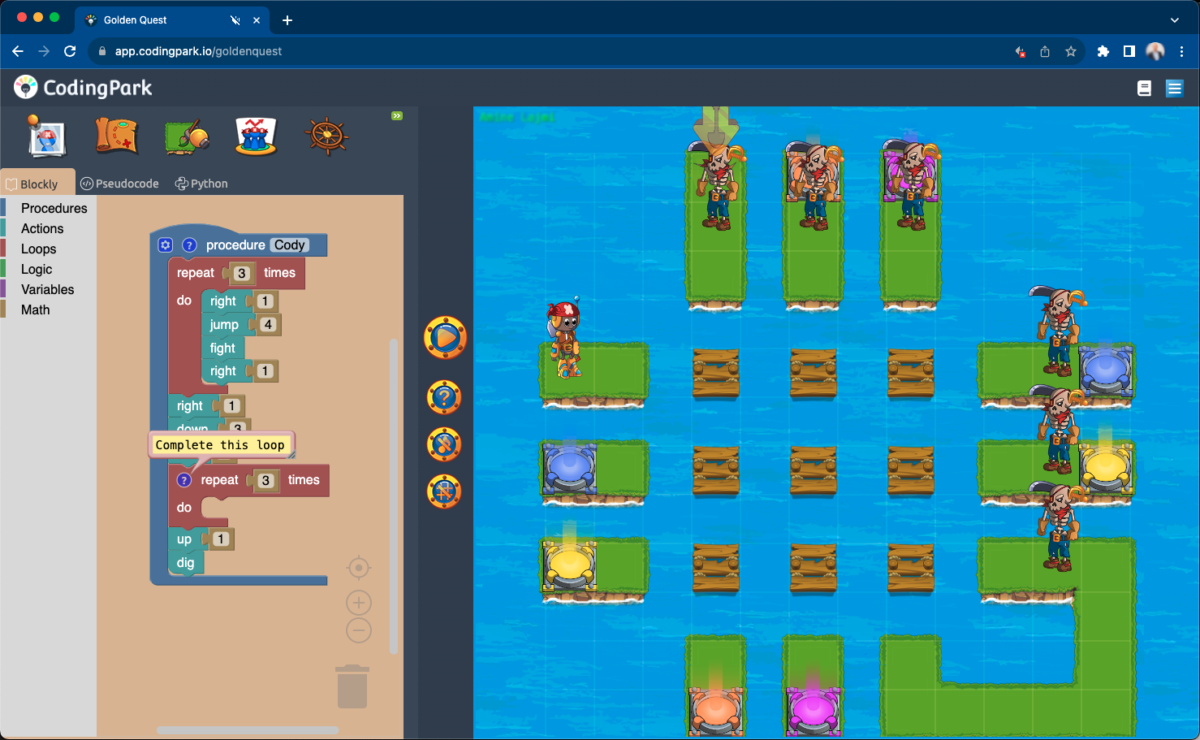
admin 2023-12-07T13:34:08+00:00Software is becoming a critical layer of all our lives; it is the language of the world. In the future, not knowing the language of computers will be as challenging as being illiterate or innumerate today. Computational thinking in particular is how software engineers solve problems, it combines mathematics, logics and algorithms, and teaches [...]